IT and cybersecurity solutions
Join the thousands of businesses that trust Calian for robust and reliable IT and cybersecurity solutions.
Discover a secure and reliable future with Calian IT & Cyber Solutions
Those in cybersecurity know that incidences nearly always occur over the weekend or in the middle of the night, so it has given us a level of comfort in knowing we have 24-hour monitoring of our systems.



Full-scale cyber capabilities + rebuild and recovery
Calian has created a security operations centre (SOC) that can easily scale to meet a customer's cybersecurity goals and requirements.
We provide the flexibility, manpower, and expertise that can work with an organization’s IT and security leaders to define, build, and manage a reliable 24x7x365 modern security operations centre that alerts on every type of threat.

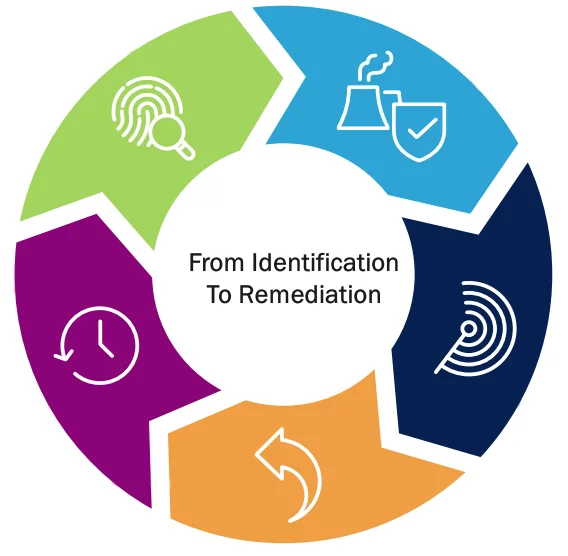
Protecting High Value Assets
- Managed firewall
- Managed endpoint
- Managed identity (MFA/SSO)
- Managed email
- Managed SASE/SWG
- Managed security awareness
- Patch Management
- Product sales and ProSrvs

Early detection with automated containment
- Managed detection and response (MDR) → XDR SOAR integration playbooks

Full-scale response
- Managed detection and response (MDR)
- Incident response retainer services

Rebuild and recover
- Incident response retainer services
- IR plans, procedures and policy development
- Tabletop exercises
- Breach and simulation exercises
- Cyber Range

Identification of risk
- Asset discovery and inventory
- Internal vulnerability management (IVA)
- External vulnerability management (EVA)
- Security, risk and compliance
- Assessments and tabletops
- Penetration testing/threat simulations
- Vulnerability and web assessments/prioritization
We move technology and security forward
Calian offers a range of customized solutions to keep your IT infrastructure running smoothly and your organization safe from cyberattacks.
IT and cybersecurity resources

Modernize and secure your IT infrastructure
Speak to an expert to empower your organization’s success in the digital realm.
Calian's global operations
With global security operations centres, Calian provides support around the clock, from day to night, enhancing security capabilities worldwide.
Current Region
Social responsibility at Calian
Committed to social responsibility.
ESG—more than a buzzword.
Our vision builds on our mission, values, historical commitment to social responsibility and key competencies. It provides a framework and focus for our activities and corporate communications related to ESG (Environmental Social Governance).
Download ESG report
Your service inspires us.
Proudly welcoming 100+ veterans to our team every year
Their expertise enriches our solutions, and hiring military spouses is our heartfelt way of giving back to the defence community. We’re committed to being there for you, in and out of uniform.
Explore opportunities

Relocating? We’ve got you covered.
4,000+ family members connected with family doctors
Our partnership with the Canadian Forces Morale and Welfare Services ensures that military family members are connected with family doctors, hassle-free.
Learn more

Building a resilient community together.
$650,000+ in corporate giving
We are woven into our community’s fabric, our support extending to renowned organizations and causes. We’re not just about business; we are about building a supportive and resilient community together.
Learn more

Engaging in research that matters.
Our contributions to significant research projects and our focus on environmental safety are unwavering. We’re front-runners in compliance with environmental laws and continually innovate to lessen our ecological footprint.
Learn more

Committed to exceeding expectations.
30+ Indigenous community engagements
With a published Indigenous engagement policy, Calian sets out the framework and guidelines for all Calian business activities while being wholly committed to meeting—even exceeding—the five per cent Indigenous participation requirement on all Federal contracts.
Learn more
Global innovation for connected, safe and healthy lives
Explore Calian's four business units below.